Is your business prepared for a ransomware attack?
Recently, the HHS Cybersecurity Program released a report detailing the impact of ransomware attacks in 2021. The results are chilling. If you think that you’re at a company that isn’t threatened by ransomware, think again.
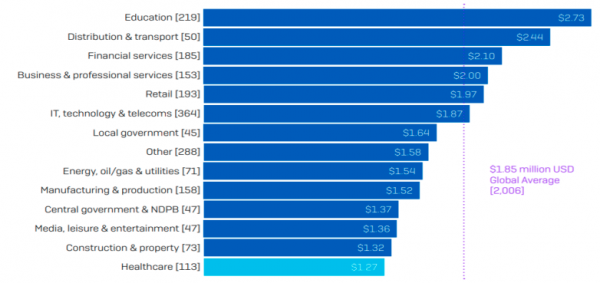
Ransomware attacks are targeting Healthcare, Manufacturing, Insurance, Technology, and Banking sectors as well as other targeted industries like Education. Knowing how these attackers operate will give you a leg up on vulnerabilities.
We’re sharing what we know about the most common ransomware variants out there. Not only should your systems administrators and IT departments know about this vital information, but all employees should brush up on the steps and precautions they can take to protect your company from malicious threats. Because some of these attacks originate from a seemingly harmless email click by an employee.
If you don’t have time to read this article, at least take our brief quiz to see if you’re vulnerable to attacks:
Are you NIST, HIPAA, or CMMC compliant? Learn more about the steps to take to integrate a company-wide infrastructure approved by governmental entities. They are great guidelines for protecting your systems from common security flaws.
Ransomware-as-a-Service
Before covering the most common tools that are used to attack organizations, we need to briefly mention the phenomenal rise in Ransomware-as-a-Service (RaaS) actors that are arming individuals with a suite of malware to carry out malicious attacks. DarkSide, Conti, and Avaddon are all current RaaS models, although they are bound to rebrand themselves to avoid detection. Many leverage a variety of combinations of variants mentioned below.
How Ransomware Works
Most ransomware variants require some human direction and intervention to target and spread through networks. But many worms can spread automatically.
Ransomware attacks generally follow the same principles. They gain access to your network through a loophole and spread through software installers, RDP servers, and other backdoor vulnerabilities. This could happen simply by an employee clicking a link in an email and downloading a file encryption virus. At that point, they gain admin-level access, encrypt your data, and lock you out.
Extortion Plans
An extortion plan follows that demands a payment, usually Bitcoin, in order to decrypt your data and return it to you. Some have a quick expected turnaround before you lose your data. Extortion doubles if the victim doesn’t meet the deadline. A new ransomware variant even comes with a ransom note and encrypts all the files in the windows system, crawling through the network.

1. Triple Extortion (used by Avaddon) encrypts, exfiltrated, and threatens data leak or DDoS attack.
2. Maze threatens to publish sensitive data on cyber-criminal forums and “has the potential to remove blacklisted files and transfer victims’ data to the attacker.”
3. Ryuk restricts system access until a payment is received. It does this by encrypting every file and infecting the victim’s machine with malware. The newest Ryuk varity is worm-like, allowing a reinfection to potentially happen.
15 Common Ransomware Variants
- Babyk
- Everest
- AKO
- Cobalt Strike (used by Conti)
- Mimikatz (used by Conti)
- Emotet (used by Conti)
- Trickbot (used by Conti)
- REvil
- Netwalker
- Maze
- Sodinokibi (used by REvil)
- Ryuk
- Bazarloader
- Mountlocker
- Triple Extortion (used by Avaddon)
Healthcare’s Ailing Systems
Ransomware in Healthcare:
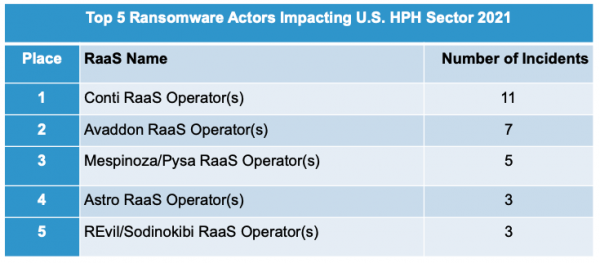
- Avaddon and Conti were the most frequently observed ransomware-as-a-service (RaaS) groups impacting the global healthcare sector
- 82 global ransomware incidents in the healthcare sector
- California experienced 12% of the ransomware healthcare incidents followed by Texas, Georgia, Illinois, and Louisiana
With 34% of attacks in the healthcare industry deciding to pay the ransom, it isn’t much of a surprise to see ransomware morph into a orchestrated cash cow for dark web organizations.
 It’s not only systems administrators that should be aware of these ransomware variants. Every employee should be familiar with the ways that these attacks happen in order to avoid clicking something malicious. Names and attacks that you should brush up on. Whether you’re in a technology position at your company or even just an employee at a company that could be attacked. Employees should have trainings that prepare them to spot phishing emails, or other odd emails that might be used to attack a company.
It’s not only systems administrators that should be aware of these ransomware variants. Every employee should be familiar with the ways that these attacks happen in order to avoid clicking something malicious. Names and attacks that you should brush up on. Whether you’re in a technology position at your company or even just an employee at a company that could be attacked. Employees should have trainings that prepare them to spot phishing emails, or other odd emails that might be used to attack a company.
Preventing Ransomware Attacks
- Multi-factor authentication for remote access to OT and IT networks
- Strong spam filters to prevent phishing emails
- Filter emails with executable files attached
- User training program and simulated attack campaigns to dissuade employees from opening malicious email attachments
- Block network traffic from malicious IP addresses
- Block URLs company-wide that are known malicious websites
- Meticulously update software, operating systems, applications, and firmware
- Patch management program
- Limit and restrict user access across networks to prevent high-level entry
- Routinely scan IT network with anti-virus and anti-malware programs
- Implement unauthoraized execution prevention by disabling macro scripts, only allowing approved executable files to launch, monitoring or blocking VPN anonymization services
Recovering From Malware
- Isolate the infected system
- Turn off other computers and devices
- Secure your backups
- Ensure that your backup data is offline, secure, and free of malware
- Power-off and segregate any other computers or devices that shared a network with the infected computer(s) that have not been fully encrypted by ransomware.
Without a fail-safe system, and a proper backup protocol, you could be in a world of pain without paying the ransom. Avoid getting yourselves into a sticky situation by familiarizing yourselves with the most common ransomware actors in the game and common ways they are carried out on your servers. If you need any help in protecting your data, reach out to us!
Request Malware Support
Fill out the form below and connect with an IT Global Services Malware Specialist.

